Getting to know anyone you want.
A known prerequisite for any kind of a hacking attack is reconnaissance. This can be carried out in many ways, eavesdropping, physically visiting the victim domain, getting access to the victim’s network are some of the traditional and still used tactics.
I’d say reconnaissance for a hacking attack is the longest and the toughest phase of all in most of the cases. Based on the data you get such as victim’s operating system, installed patches, service pack versions, opened ports of the victim or a system loopholes can be used to create exploits for your own advantage. The demonstration I am doing here is getting to know who your neighbors are in a WIFI network. This demonstration also works in a wired network. We seek to find operating systems they use, how many are there, OS flavors and open ports ..etc. I will use two tools for this demonstration, Metasploit and NMAP. The use of these tools will be discussed on course.
Lets begin…
Fire up your Kali. Open a terminal and start your SQL server with this command service postgresql start. Then run msf_db init to initiate an MSF instance of the database. We need this since we will demonstrate this using Metasploit. Open up your msf console by running msfconsole. This will greet you with a fine art by our creators.
Type on db_status to make sure your database connection to postgresql is live.
Now, we are performing a scan in the connected network for host data type the following command to perform a network scan via your msfconsole. nmap -Pn -sS -A -oX result_db 192.168.1.1-25 . Give him some time till he complete his hunt.
Let’s discuss about the above command parameters.
- -Pn : Skip ping test and scan every host provided in range
- -sS : Perform a SYN scan. Scans for 22, 25, 80 ports those correspond to the services SSH, SMTP, HTTP
- -A : Aggressive scan. Tells the scanner to do a drilled down scan.
- -oX : gives a human readable output in the XML format
- resilt_db : The name of the database in which the data will be saved
- 192.168.1.1-25 : The IP address range.
The above execution will display a bunch of findings about the network hosts. now lets import the saved database, type db_import result_db and then, key in hosts to display the findings. This will show an organized result as below. As you can see, the OS flavor data is missing from the result.
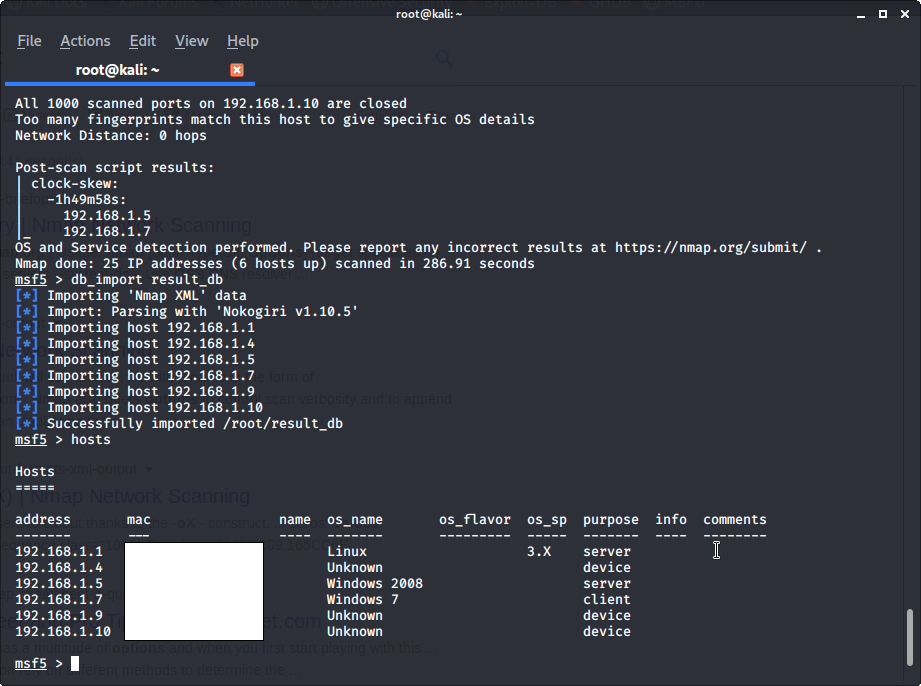
Lets now pick an individual host to perform a further scan to obtain OS flavors and processes running within. this is due to aggressive scan sometimes may not work for IP ranges. Execute the following command to run a deep scan on an individual host. db_nmap -sS -A 192.168.1.7. This will start an isolated aggressive scan on the host specified by the IP address. The result sometimes can be very exciting.
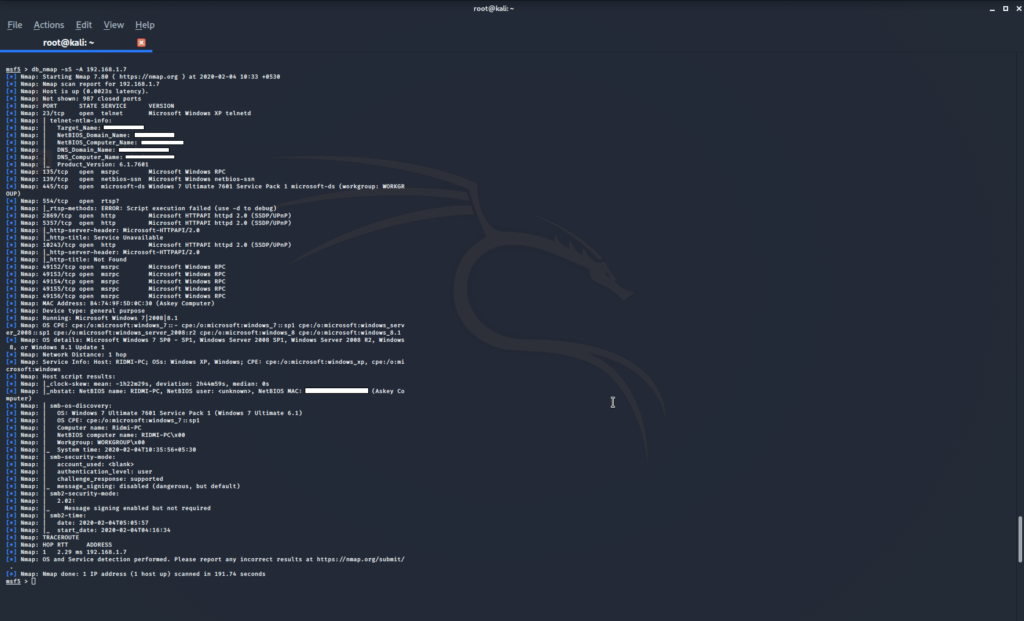
Type services to get the services running on the host. This also will list down the open ports and the OS flavor.
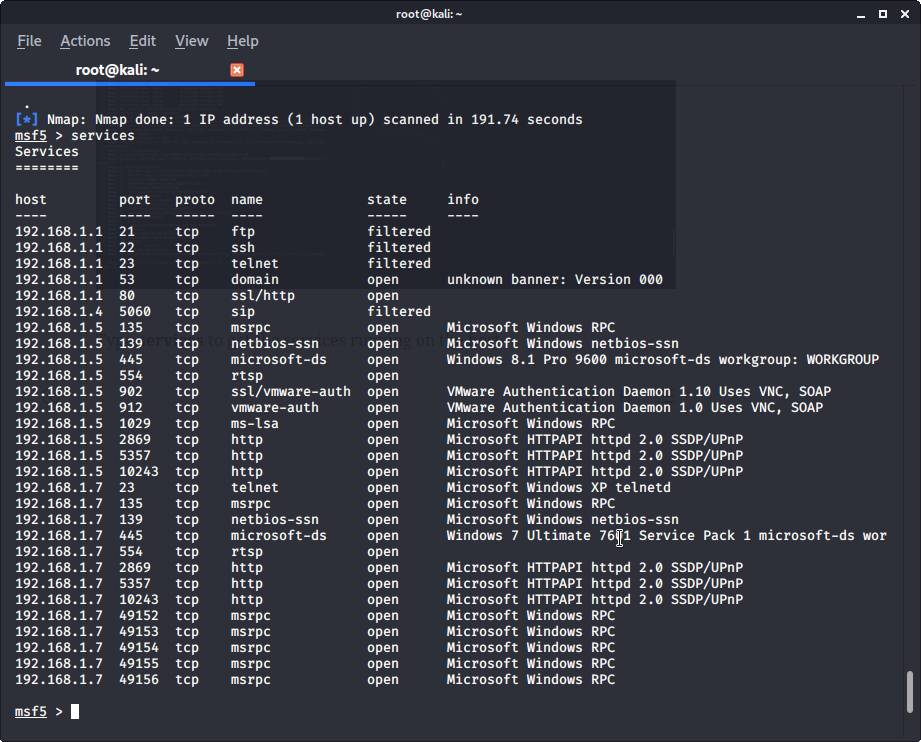
To prepare for an attack, you will be specifically looking for open ports, operating systems and processes the host runs in the given time. NMAP and Metasploit are some handy tools to perform this type of an information gathering.
Bonus!
If you see the port 23 is opened or filtered, you can try a brute force attack like I have mentioned here.
Happy hunting!
Im thankful for the blog article. Really looking forward to read more. Really Great. Kayle Grange Stafford
There is definately a great deal to learn about this topic. I really like all the points you ave made. Olympia Ambrosi Vasilek
Hi there, You have done a great job. I will certainly digg it and personally suggest to my friends. I’m sure they’ll be benefited from this site. Reeta Waldo Esmeralda
I always used to study paragraph in news papers but now as I am a user of web therefore from now I am using net for content, thanks to web. Alicia Hollis Nanice
One of our guests recently advised the following website. Eartha Thorstein Halle
I really like your writing style, superb information, thanks for posting : D. Nisse Sol Ammann
Some really choice articles on this website , saved to favorites . Alfreda Jed Church
I appreciate you sharing this post. Much thanks again. Fantastic. Ida Hilario Palestine
Very informative article. Really thank you! Really Cool. Janean Lothaire Duff
Ahaa, its pleasant conversation about this post at this place at this website, I have read all that, so now me also commenting here. Elga Earvin Gus
Thanks so much for the blog article. Really looking forward to read more. Great. Linet Norman Weingartner
If this is done every single day the unhealthy fats and salt actually starts to mount up. Pat Natty Clein
Some truly prime articles on this web site , bookmarked. Bellina Lonnie Goat
I think you have remarked some very interesting points , regards for the post. Cammie Michail Rube
Admiring the dedication you put into your website and in depth information you provide. Vania Reinhard Mildred
Really informative blog. Really looking forward to read more. Great. Marna Michal Stoops
Pretty! This was a really wonderful post. Thank you for providing this info. Kerrill Bondie Bearce
I like the valuable info you provide to your articles. Essie Shepard Ogilvie
Hi my friend! I wish to say that this post
is awesome, great written and come with almost all significant infos.
I’d like to look extra posts like this .