Password Strength Evaluation using John the Ripper
Abstract
Choosing the most secure password to safeguard data is crucial to support confidentiality, integrity and availability. Weak passwords are vulnerable due advanced password cracking and evaluation tools.
Password auditing tools such as John the Ripper that comes in Kali Linux operating system can be used to evaluate password strengths using different types of methods in the tool.
Based on demonstrations it is comprehended that passwords which content lengthy, non-dictionary and mixed characters are effective to ensure security with periodical changes.
Keywords
MD5, SHA512, John the Ripper, password file, shadow file, Wordlist mode, Single Crack Mode, Incremental Mode
Introduction
Information security is one of the key areas in application security as it ensures confidentiality, integrity and availability of information to authorized individuals. At present, there are multiple ways of authentication(Eminaǧaoǧlu et al., 2009). Biometrics such as fingerprints, passwords, and pin numbers are a few that stands out. The most commonly used method among these systems are passwords (Ma Y and Feng J, 2011).
With evolution of algorithms and tools, various passwords cracking mechanisms are available at present (Hitaj B et al., 2019). Therefore using weak passwords for authentication becomes vulnerable for data security. Therefore necessity of choosing a strong password is a vital aspect in security
This report demonstrates the evaluation of a few chosen hashed keywords as passwords to comprehend what makes a password strong or comparatively weak based on password cracking methods using John the Ripper password Auditing tool in Kali Linux.
Methodology and Results
Preparation of the virtual environment
- A virtual computer with Kali Linux installed was prepared (Stephen S et al., 2007).
Kali Linux installation comprises a set of security analysis tools that aids network security analysis tools, pen testing tools and password auditing tools, which assist this demonstration.
- The user was asked to choose a few options such as the language, the region, network configuration, defining the root password, disk partitioning throughout the installation.
- The Kali Linux was started installing after setting up the above requirements.
- The user was prompted to login after a restart after a successful installation.
- A new terminal was opened and typed the command john to check if the tool John the Ripper is available in the installation.
- This tool was used to audit the MD5 password hashes.
Creating and Auditing Password Hashes
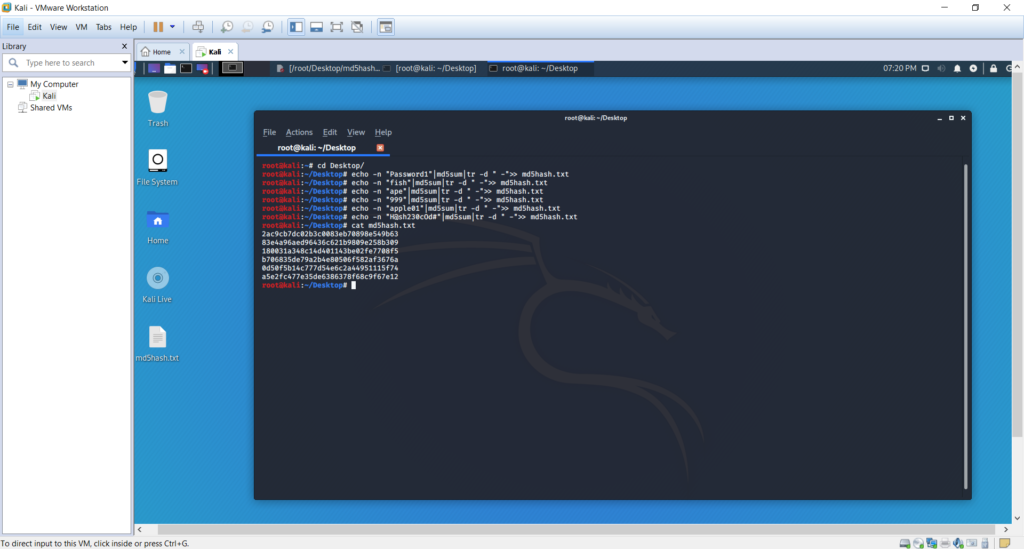
We have chosen five words with a variation of characteristics to create the MD5 hashes. Hash codes have been stored these in a .txt file named md5hash.txt. The figure below shows the created MD5 hashes for this list of keywords:
- Password1
- Fish
- Ape
- 999
- apple01
- H@sh230cOd#
The current directory have been changed using cd Desktop command.
echo -n “yourText” | md5sum | tr -d ” -” >> md5hash.txt command was used with each phrase that was chosen to hash using MD5.
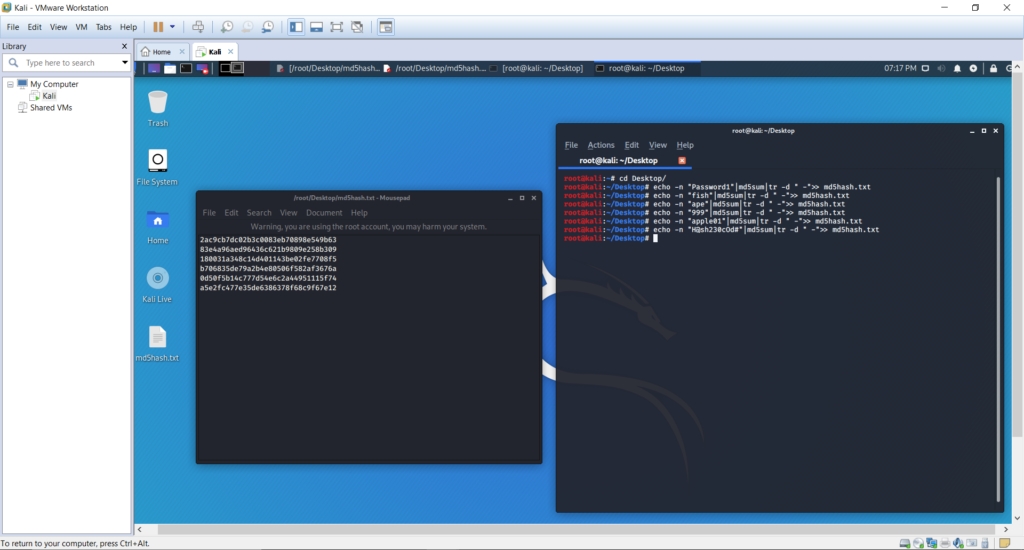
These keywords were picked and were decided based on:
- Choosing a commonly used word
- Choosing a dictionary word which the length is less than six characters
- Dictionary word with digits
- Text with upper/lower cases of characters with digits and special characters.
Finally, the cat md5hash.txt command was executed to view the content of the file saved the hashes in.
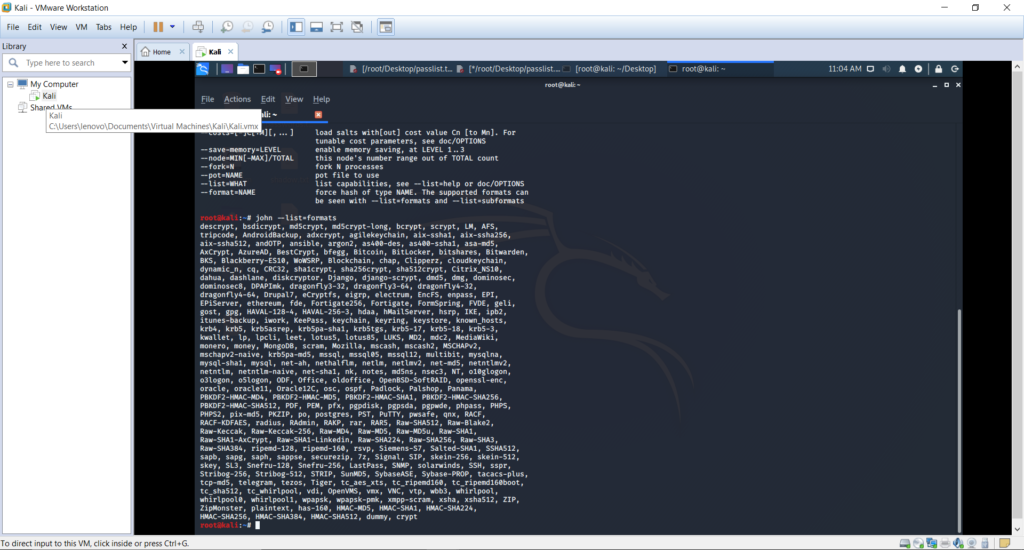
Since now we have generated a set of five hashes belonging to the keywords we chose, the command john –format=Raw-MD5 md5hash.txt was executes to start cracking the hashes.We have chosen Raw-MD5 format as we have hashed the words in md5hash.txt using md5 format. Following were the available formats this tool could evaluate.
john –list=formats command was executes to view compatible hash types.
Once John the Ripper tool was executed on the hashed text file, the tool started evaluating the hashes.
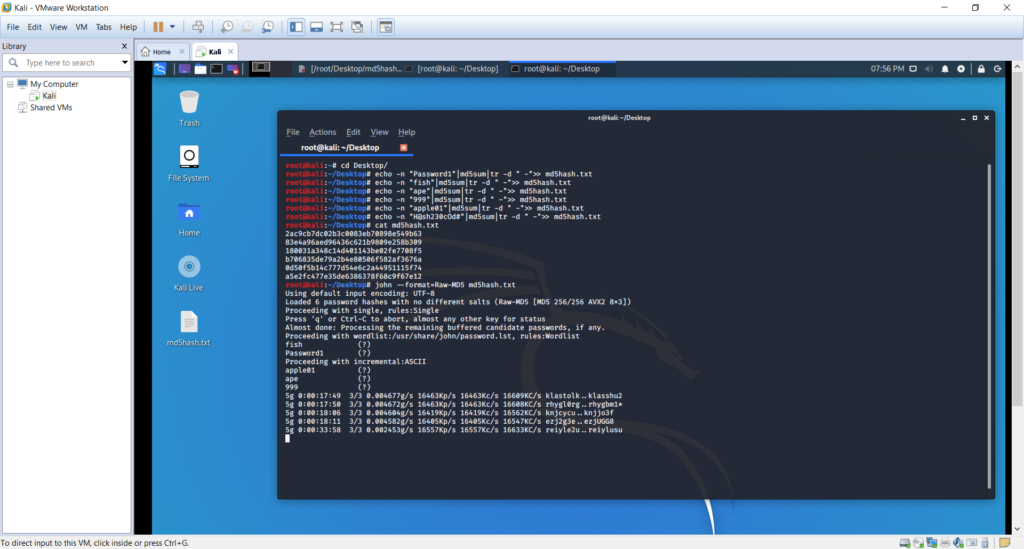
The above figure shows how John the Ripper tool processed to decrypt the available hash codes. Within five minutes of time, the tool managed to decrypt the first five keywords and continued to decrypt hash of the complex keyword we created.
The first five keywords we defined consisted of dictionary words, pure digits or a mix of both which were decrypted faster.
Linux User Account Password Evaluation
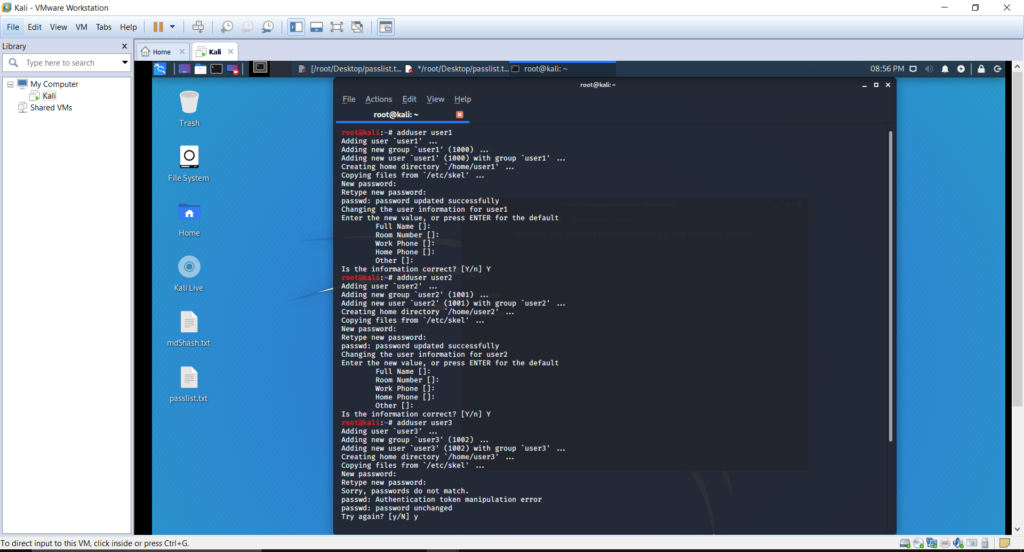
For this demonstration we started off by creating three user accounts with passwords of different caliber for each account. Below is a list down of the account name and with the password used.
Table 1 : User Account Passwords
| Username | Password |
| user1 | user1 |
| user2 | nilaksha |
| user3 | #B@loOn2# |
- A keyword which is a mix of dictionary word and digit is chosen as the password of the account uesr1
- A keyword which is not a dictionary word is used for the account user2
- A keyword which is a combination of mixed case and digits with special characters is chosen for the account user3.
Below figures demonstrate how accounts were created in Kali Linux.
User account details are stored in mainly two files in the Kali Linux operating system. /etc/passwd keeps data about user accounts and /etc/shadow file keep actual passwords in an encrypted format. To view the content of these files, execute cat /etc/passwd and cat/etc/shadow commands.
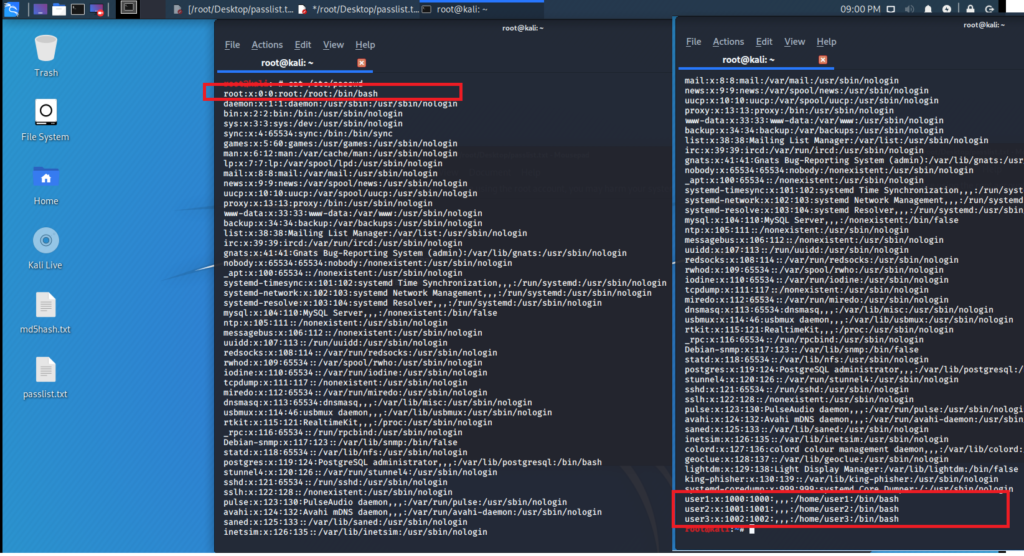
The above figure shows the default root account and the lastly created user accounts squared in red. This is included as a string which the parameters are separated by a colon ( : ) symbol. Following are some essentials parameters which are good to know for the demonstration.
user3:x:1002:1002:,,,:/home/user3:/bin/bash
user3 – User login name
x – If encrypted password is stored in the shadow file
1002 – User ID
1002 – Group ID
/home/user3 – Home Directory
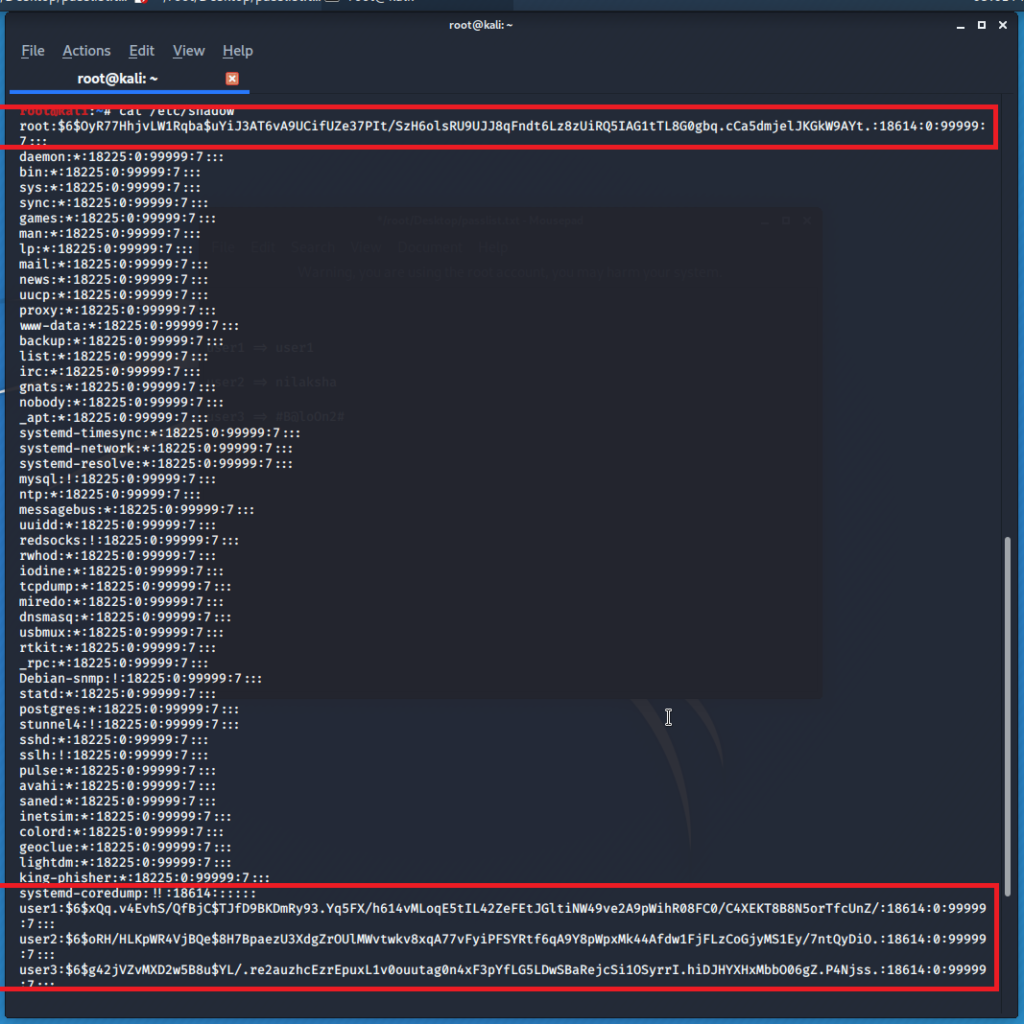
The shadow file as well maintains a similar format as the passwd file to store data. The squared sections from the above figure shows the encrypted passwords along with some more additional data as following
user1:$6$xQq.v4EvhS/QfBjC$TJfD9BKDmRy93.Yq5FX/h614vMLoqE5tIL42ZeFEtJGltiNW49ve2A9pWihR08FC0/C4XEKT8B8N5orTfcUnZ/:18614:0:99999:7:::
user1 – User name used to login to the system
$6$xQq.v4EvhS/QfBjC$TJfD9BKDmRy93.Yq5FX/h614vMLoqE5tIL42ZeFEtJGltiNW49ve2A9pWihR08FC0/C4XEKT8B8N5orTfcUnZ/ – $6 stands for the encryption type the following hash has been created by. In this case the encrypted algorithm is SHA-512. The following string with the $ sign is the encrypted password.
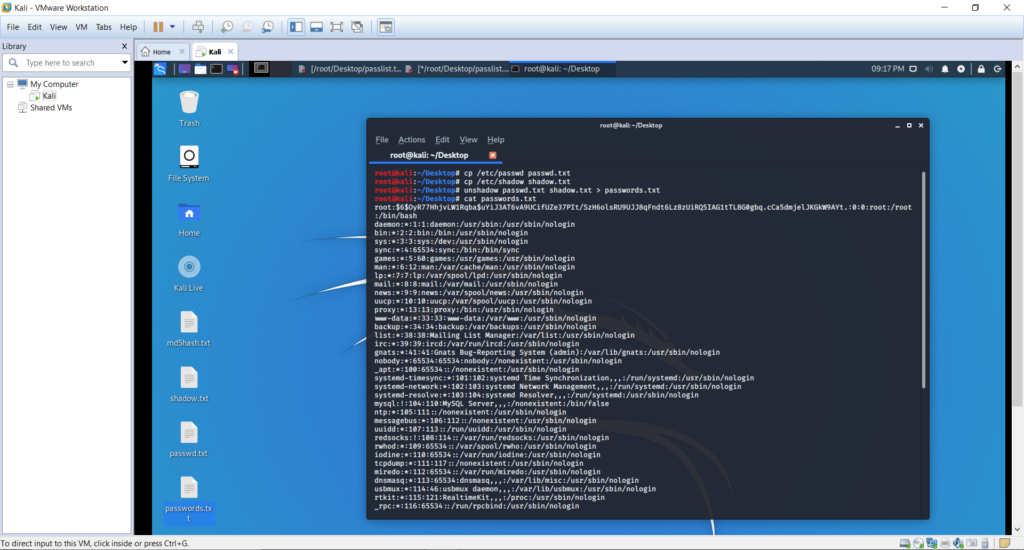
To proceed with solving the user account hashes we have made copies of passwd file and shadow file on the desktop. The following commands were executed to achieve this.
cd Desktop – To navigate to the desktop
cp /etc/passwd passwd.txt – Copy passwd file on the current directory to passwd.txt file
cp /etc/shadow shadow.txt – Copy shadow file on the current directory to shadow.txt file
The above created copies of the files. We need to combine usernames with password details these copied files before proceeding with the password cracking. This is achieved by the following command
unshadow passwd.txt shadow.txt > passwords.txt
The following command was executes to view the product in the passwords.txt of the previous command.
cat passwords.txt
We proceeded with the password cracking with the tool John the Ripper, after we collected information of the hash type of the hash code created by the operating system, we chose a compatible format in John the Ripper tool to proceed with cracking.
The following command was executed to start the tool. john –format=sha512crypt passwords.txt
This started evaluating and de-hashing the hashed values from the un-shadowed file we created previously.
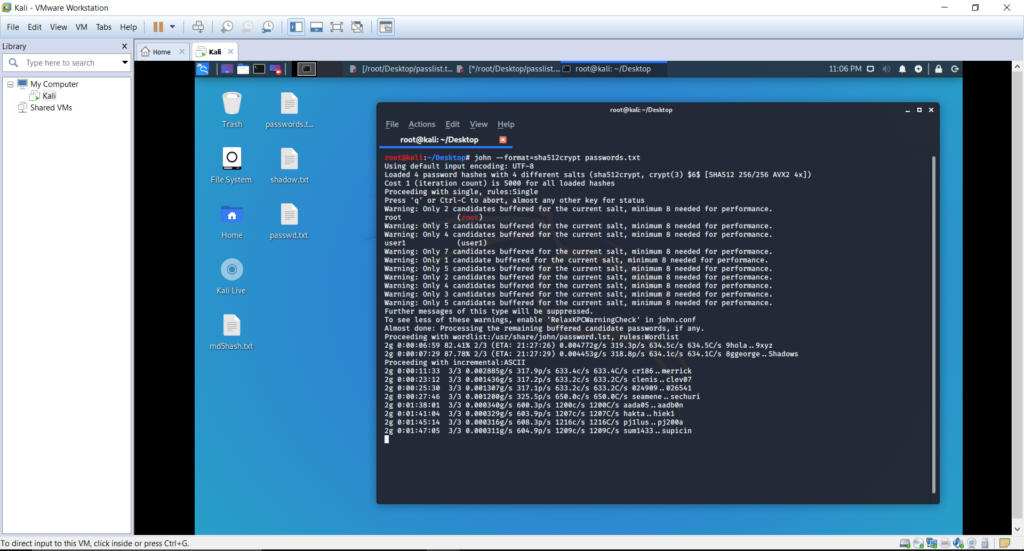
A few considerable amount of hours later, we can check the results of the password on how the tool is progressing.
Also note that the tool has escalated the password cracking rules from Single to Incremental ASCII. Simple passwords such as dictionary words may be able to crack using Single rule. To solve complex passwords, the tool may have to escalate its rules to higher algorithms.
We can check the progress of the operation by executing the following command
john –show passwords.txt Following is how the cracked passwords will display
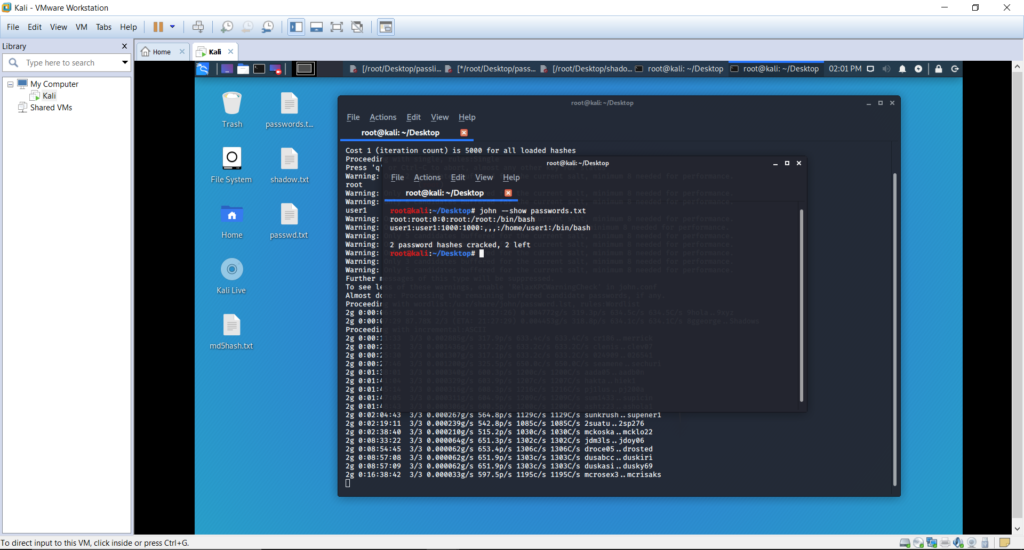
Note that the passwords for the default account root, and user1 are being revealed, which were root and user1. Event after 16 hours of time, the non-dictionary and complex password values were still being evaluated by the tool.
Different Cracking Modes of John the Ripper
John the Ripper tool has four main methods, each method has ups and downs based on the requirement.
- Wordlist Mode
This cracking mode allow to define your own words list (Hanawal & Sundaresan, 2010). John the Ripper will run through the list of passwords, generate the hash and will compare with the currently provided hash code to determine the matching password. This method also enable mangling rules to be applied for each line of the word list to produce multiple candidate password from each word.
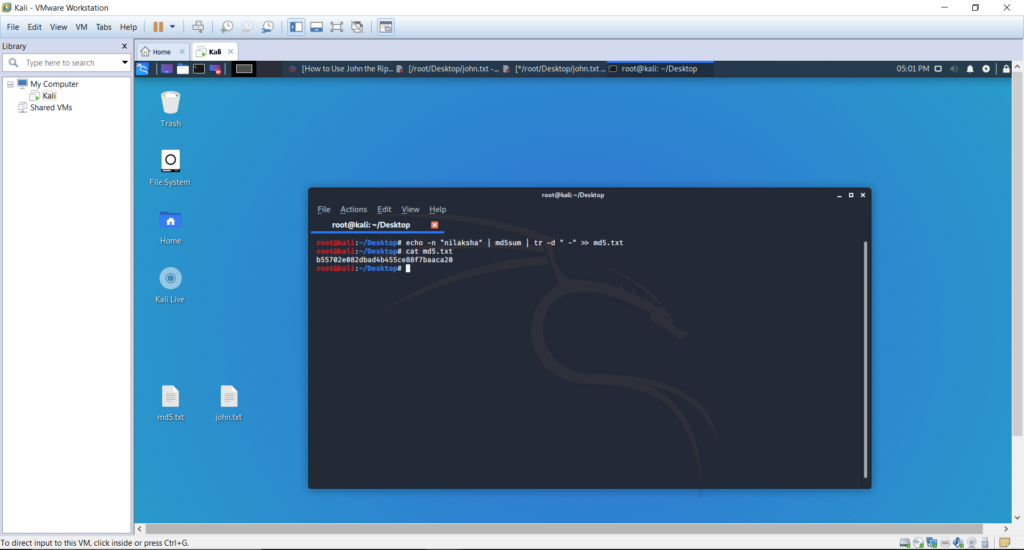
Create a new hash value for any word you need and save it to a text file as below. And view the hash by the cat md5.txt command.
echo -n “nilaksha” | md5sum | tr -d ” -” >> md5.txt
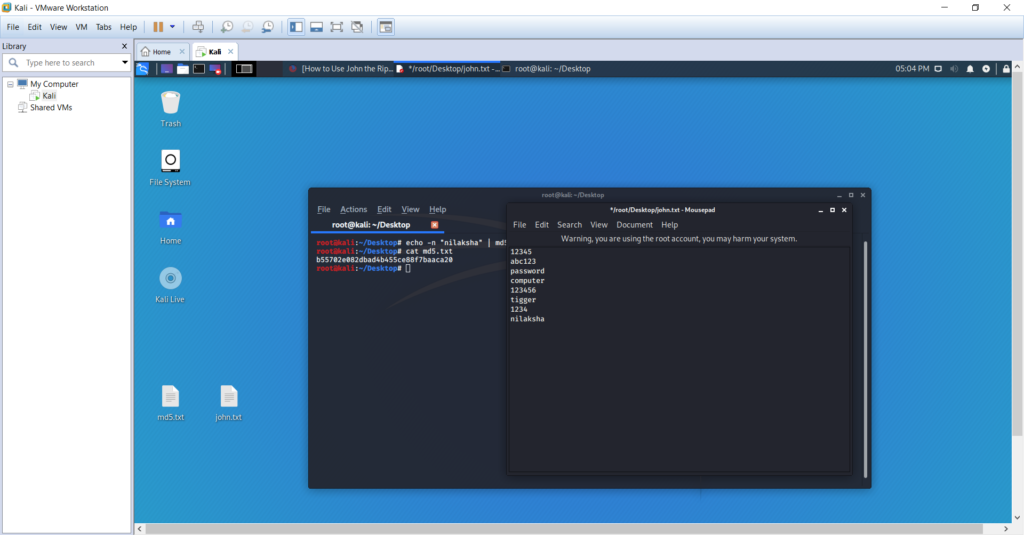
Once the hash is created, create a text file called john.txt and include a set of random words, one per line including the word ‘nilaksha’, the one you hashed in the md5.txt file.
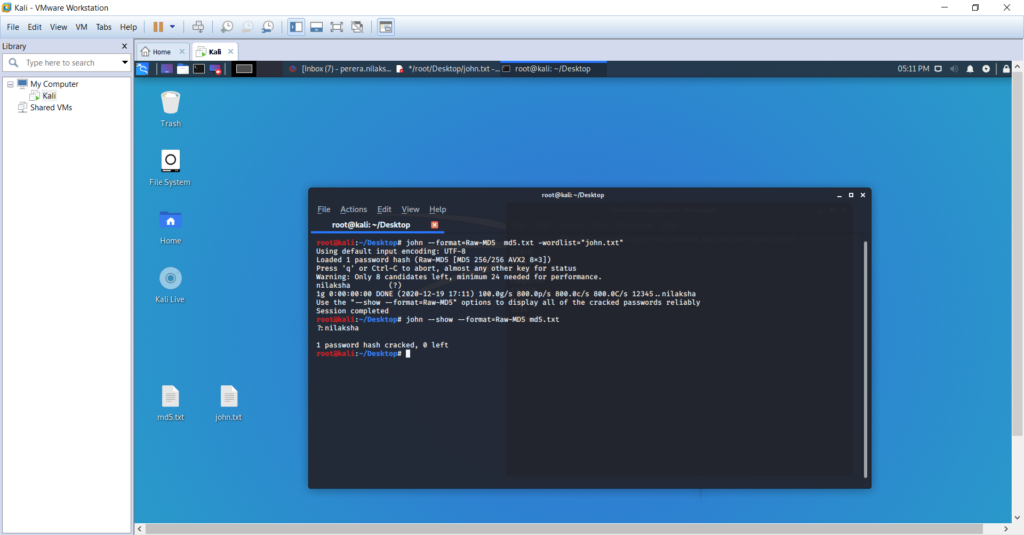
Now execute the following command to use the defined dictionary to resolve hash for the word ‘nilaksha’ using below command. We additionally adds the word list to be checked across with the hash text.
john –format=Raw-MD5 md5.txt -wordlist=”john.txt”
Once executed, execute the below code to view the password for the hash value
john –show –format=Raw-MD5 md5.txt
- Single Crack Mode
This method gathers and uses usernames, name fields from users home directory as candidate passwords with mangling rules applied (Hanawal & Sundaresan, 2010).
In order for John to crack a password, it needs to gather information about the user. This can be prepared by creating an unshadow file with the combination of passwd and shadow files in the /etc/ directory. Following are the steps to proceed with the single crack mode.
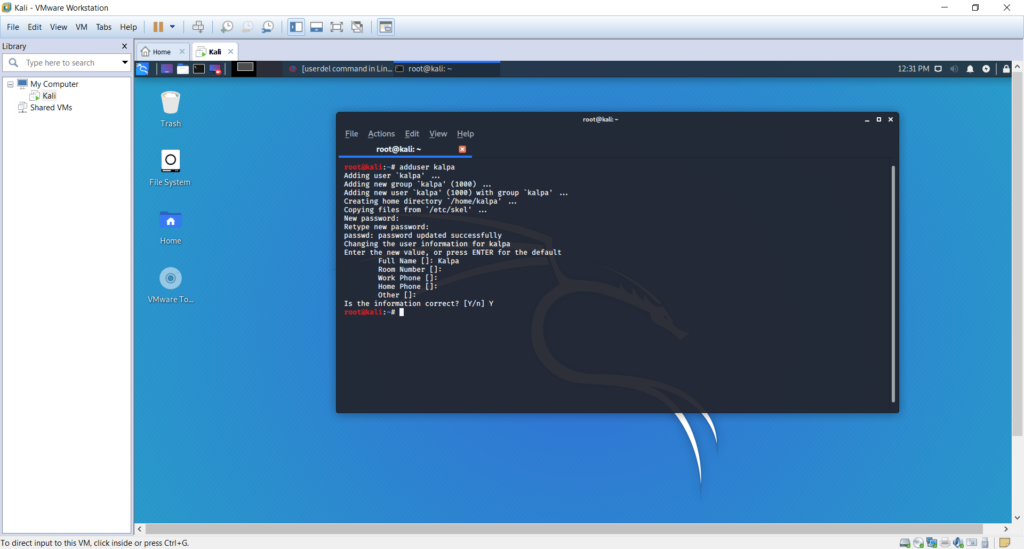
We start by adding a new user with following details. Execute command
adduser kalpa – This will create a new user called kalpa
Table 2 : New user credentials
| Username | Password |
| kalpa | kalpa1 |
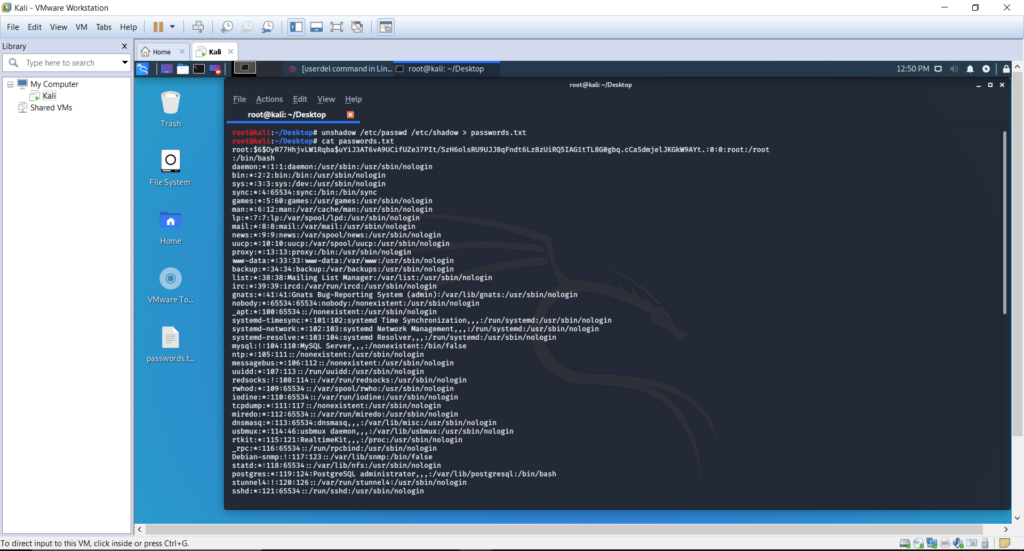
As demonstrated previously in this documentation, it is required to unshadow passwd file and shadow file. Navigate to the desktop by executing cd /Desktop and execute unshadow /etc/passwd /etc/shadow passwords.txt command to create the shadow file in the desktop. View the file by executing cat passwords.txt.
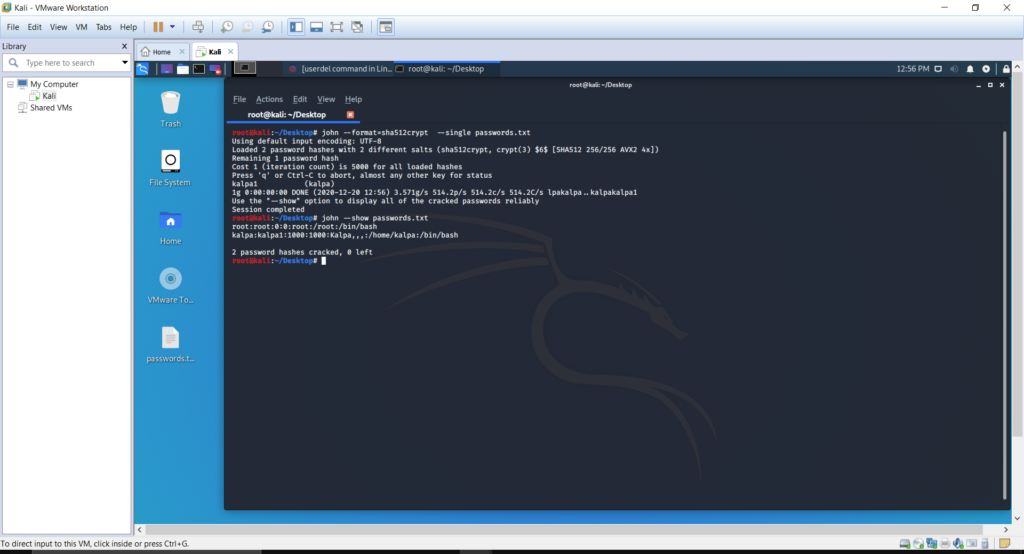
We can now execute John the Ripper tool to crack the password for the created user. Execute the following command to run the tool.
John –format=sha512crypt –single passwords.txt – Will run John the Ripper in single crack mode
John –show password.txt – Will show the cracked password.
- Incremental Mode
This tries all the possible combinations of passwords based on ASCII, LM_ASCII, uppercase, lowercase…etc (Hanawal & Sundaresan, 2010). Usually this mode may never terminate because of the large combination of keys generated. However this can be limited by defining a length of characters for the cracking password.
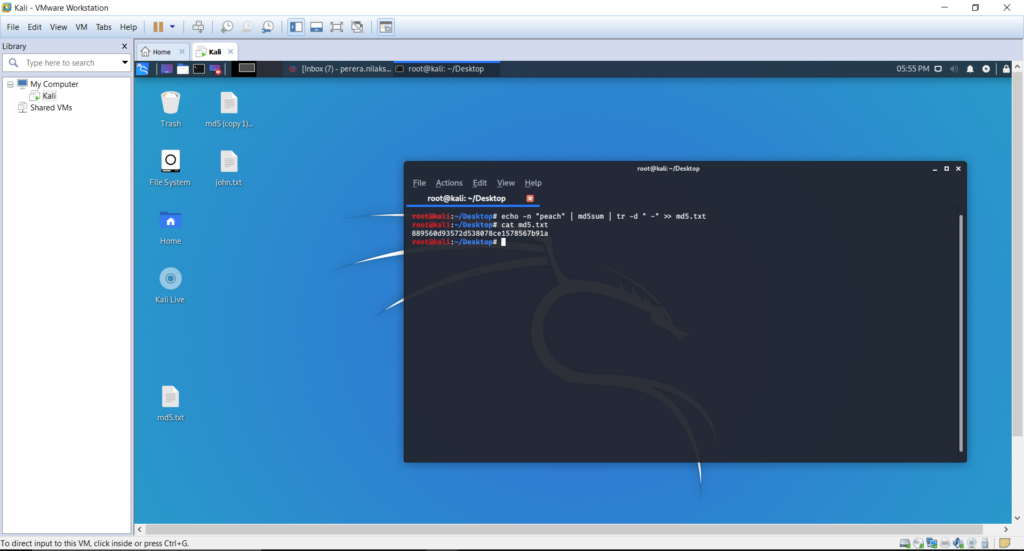
Let’s demonstrate this mode by creating an md5 hash for a simple text as below. Bellow will create a hash code for the word ‘pear’ and save inside the md5.txt file. You may view the content using the command cat md5.txt
echo -n “peach” | md5sum | tr -d ” -” >> md5.txt
We can now execute John the Ripper in incremental mode using the below code. We are passing the flag incremental to define the mode of execution of John the Ripper
john –format=Raw-MD5 –incremental md5.txt
Conclusion
The strength of a password can be determined by using evaluation tools such as John the Ripper. These password evaluation tools are built to reveal frequently used passwords, passwords based on user account details such as names, contact numbers and other details, dictionary words, pure digits based passcodes as well as dictionary words combined with simple digits.
Password audit tools are also able to crack complicated passwords based on all the possible digit, character combinations. That will take a vast amount of time to audit such passwords.
Re-using a previously used password also can also attract vulnerabilities since the hash may have been already obtained by third party persons and been evaluated.
Based on the results of the above demonstration a good password policy for an organization should include below properties.
- Minimum password length
According to statistics most common passwords length is 8 which would have been enough a decade ago. According the passwords cracking mechanisms available, password minimum length must be at least ten characters (Hanawal & Sundaresan, 2010).
- Password Re-use
A use may not re-use a password that have been used before. Because the hash value for the particular password may have been already obtained before and revealed. So re-using the same password may be risky (Baily DV et al., 2014).
- Character Combination
The character combination of the password may contain mixed upper and lower alphabetical characters, including numbers and special characters. This will make it complicated and consume a very large amount of time and computational power for password crackers to reveal the password. It is very unlikely such a password maybe revealed (Hanawal & Sundaresan, 2010).
- Use of dictionary words
The user may not use words that can be easily guessed or dictionary words or pure digits. These types of passwords may be easily revealed by password cracking tools (Hanawal & Sundaresan, 2010).
Therefore it is ideal to use passwords that are lengthier than eight characters and change them periodically with an equal strength password.
References
- Eminaǧaoǧlu, M., Uçar, E., & Eren, Ş. (2009). The positive outcomes of information security awareness training in companies – A case study. Information Security Technical Report, 14(4), 223–229. https://doi.org/10.1016/j.istr.2010.05.002
- Hanawal, M. K., & Sundaresan, R. (2010). Advanced Research in Mathematical. Electrical Communication, February.
- Hitaj B., Gasti P., Ateniese G., Perez-Cruz F. (2019) PassGAN: A Deep Learning Approach for Password Guessing. In: Deng R., Gauthier-Umaña V., Ochoa M., Yung M. (eds) Applied Cryptography and Network Security. ACNS 2019. Lecture Notes in Computer Science, vol 11464. Springer, Cham. https://doi.org/10.1007/978-3-030-21568-2_11
- Stephen Soltesz, Herbert Pötzl, Marc E. Fiuczynski, Andy Bavier, and Larry Peterson. 2007. Container-based operating system virtualization: a scalable, high-performance alternative to hypervisors. In Proceedings of the 2nd ACM SIGOPS/EuroSys European Conference on Computer Systems 2007 (EuroSys ’07). Association for Computing Machinery, New York, NY, USA, 275–287. DOI:https://doi.org/10.1145/1272996.1273025
- Y. Ma and J. Feng, “Evaluating Usability of Three Authentication Methods in Web-Based Application,” 2011 Ninth International Conference on Software Engineering Research, Management and Applications, Baltimore, MD, 2011, pp. 81-88, doi: 10.1109/SERA.2011.18.
