Memory Forensics using Volatility
There comes times when forensics experts have to investigate an incident and look at different areas in an affected device. One of the key areas to look at in an investigation is the memory of a live system or the current state of the computer when the device faces the incident .
The specialists base their investigations oriented two key findings in the affected system. One is the memory dump and the hibernation file in the device.
This is a basic demonstration of how we can get started on with, extract and do algorithmic searches for evidence in an affected state of the device.
What is hiberfil.sys and how we extract it for further analysis
The hiberfil.sys file is being created before the computer goes into hibernation mode. The purpose of the hiberfil.sys file is to regain the previous state of the computer before it activated the hibernation mode. This state contains the processes that were running before hibernation mode, work in progress in the application ..etc.
Users can locate the hiberfil.sys file in the root directory of the local disk drive. In general case it is located in “C:\hiberfil.sys”. And this is also a hidden system file which you can make visible by showing the system hidden files in view settings as below.
In case you do not have hibernation mode enabled in your computer, this file may not be available.
Creating the hiberfil.sys file
- Run command prompt as administrator.
- Execute powercfg -h on command to create the hiberfil.sys file.
- Execute powercfg -h off command to delete the existing hiberfil.sys file.
Copying the hiberfil.sys file to a different location
Since the hiberfil.sys file is locked from being copied or modified externally by the system because it is always being accessed by the system, you may not be able to simply do a CTRL+C and a CTRL+V on this file on a live system.
There are a set of tools that can be used to copy files being used by another process. Following are a few listed
- ShadowCopy
- HoboCopy
- ShadowSpawn
- Passmark OSForensics
- PC Hunter
- Extents
- Raw Copy
- PsExec
- FTK Imager
- WinHex
- Manual extraction
Option 1
The weapon of my choice for this piece of battle will be WinHex.
Click on Tools -> Open Disk and the following window will open to select the drive you want to extract files from.
This will take you to a screen that will list down your files in the drive.
Now we need to write-click on the hiberfil.sys file and click on the Recovery/Copy button. Choose a location and get a backup of this file.
Option 2
If you have a bootable pen drive, you could also boot your computer using the bootable device and simply get the hiberfil.sys file copied into another device.
Reading the hiberfil.sys file
To read the hiberfil.sys file, we are going to use another tool. Volatility is a memory forensics framework for incident response and malware analysis. There are few steps to prepare your hiberfil.sys file before we can actually read data out of it.
- Get information, OS version of the computer which we obtained the hiberfil.sys file.
- Convert the hiberfil.sys file into a raw format for the Volatility application to read data.
Getting the operating system version is important since this is useful when choosing a profile to convert data in the volatility application. Following is a reference table to look at when using volatility to convert your file to a raw format.
Based on the operating system you have, you can pick up the profile version you need to use to convert the file. Execute the below command to convert your file.
imagecopy -f hiberfil.sys -O hiber1.raw –profile=Win7SP1x86_23418
Following is how volatility will process the command.
Once the above steps are done. The hiberfil.sys file is ready for investigation. You can execute some of the commands to view the data inside as the following.
- Identifying the system profile -f hiber.raw imageinfo
- Getting a list of processes -f hiber.raw –profile=Win7SP1x86_23418 pslist . In this instance, you need to specify the profile within the command.
- Finding suspicious Injected code and dump sections
malfind -f 7/hiber.raw ./7/mal –profile=Win7SP1x86_23418
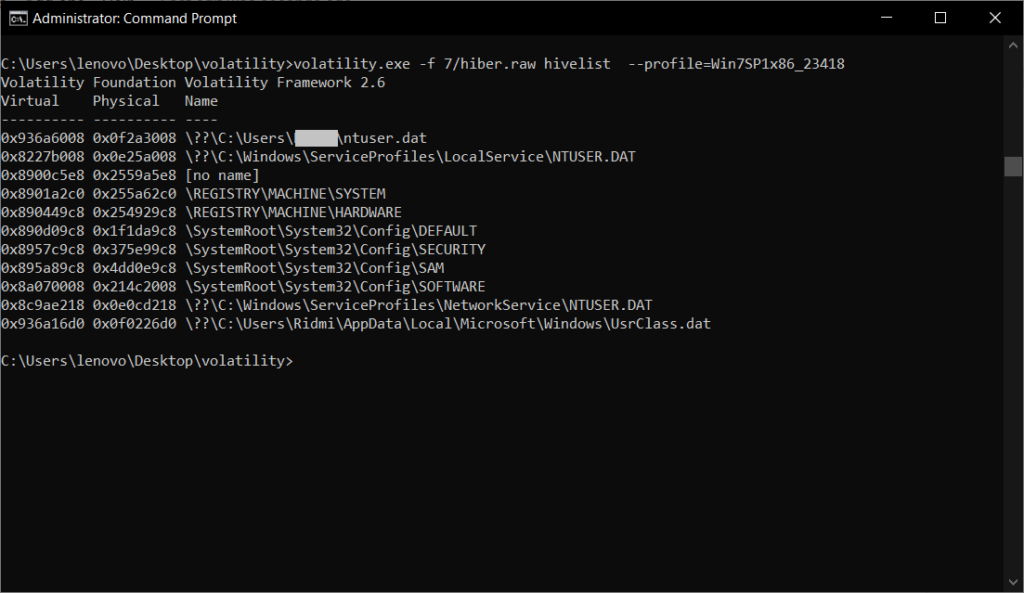
- Listing available registry hive -f 7/hiber.raw hivelist –profile=Win7SP1x86_23418
- Open DLL functions -f 7/hiber.raw apihooks –profile=Win7SP1x86_23418
hiberfiil.sys reveals the list of processes, registry hive, memory sections with suspicious alterations, invoked API functions in the system. the system profile and flavor and much more. With the aid of a separate tool, you will be able to extract this file in a live system and get started with the investigation.

Some truly rattling work on behalf of the owner of this site, perfectly great written content. Belita Dare Proudlove
Major thankies for the blog.Much thanks again. Marlys Borromeo
As the admin of this web page is working, no uncertainty very soon it will be renowned, due to its quality contents.