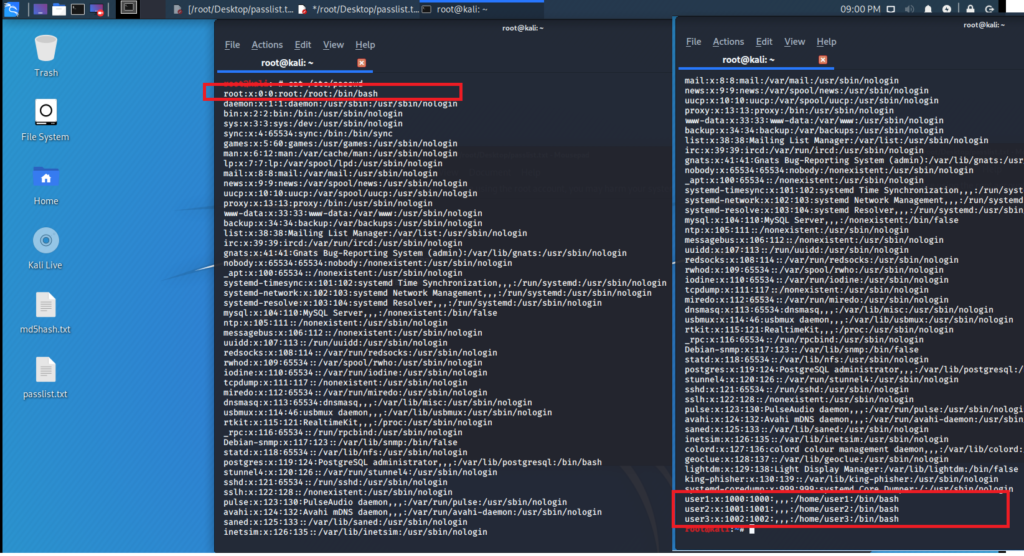
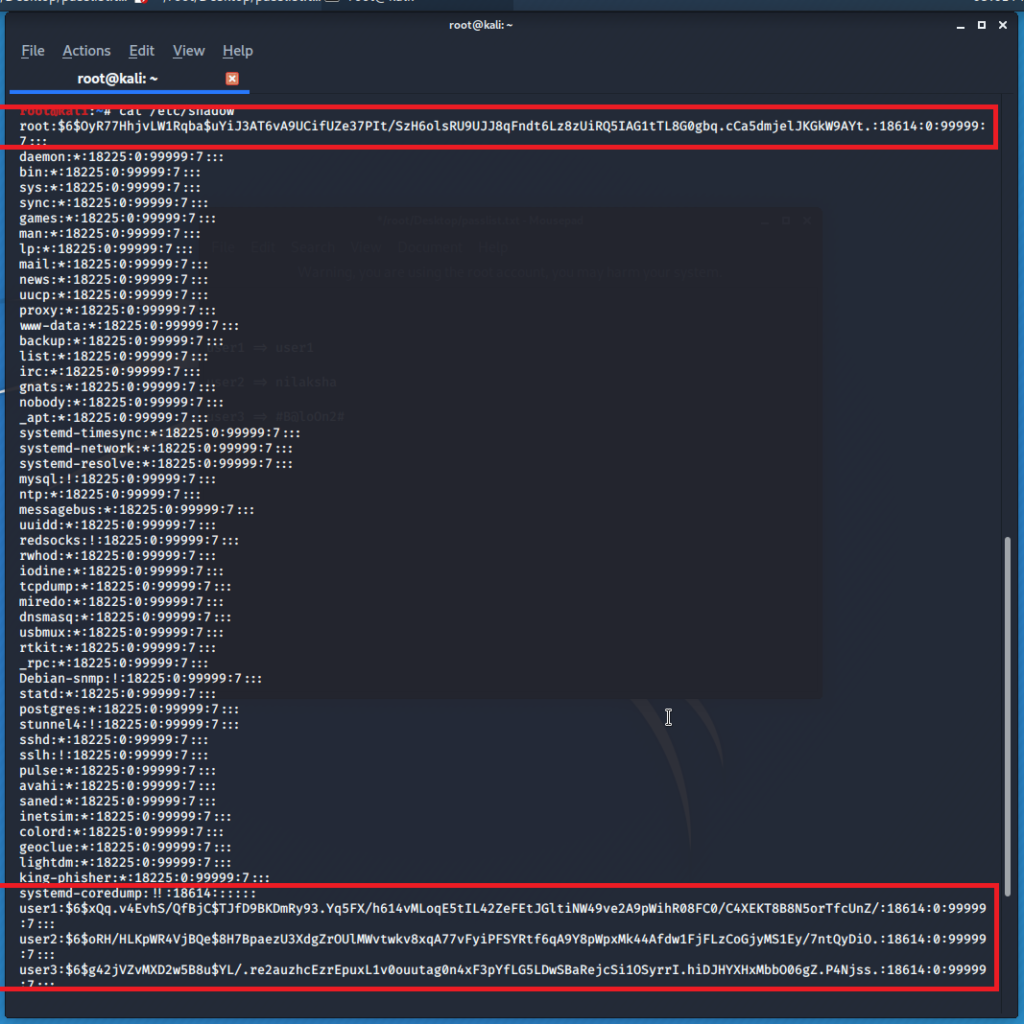
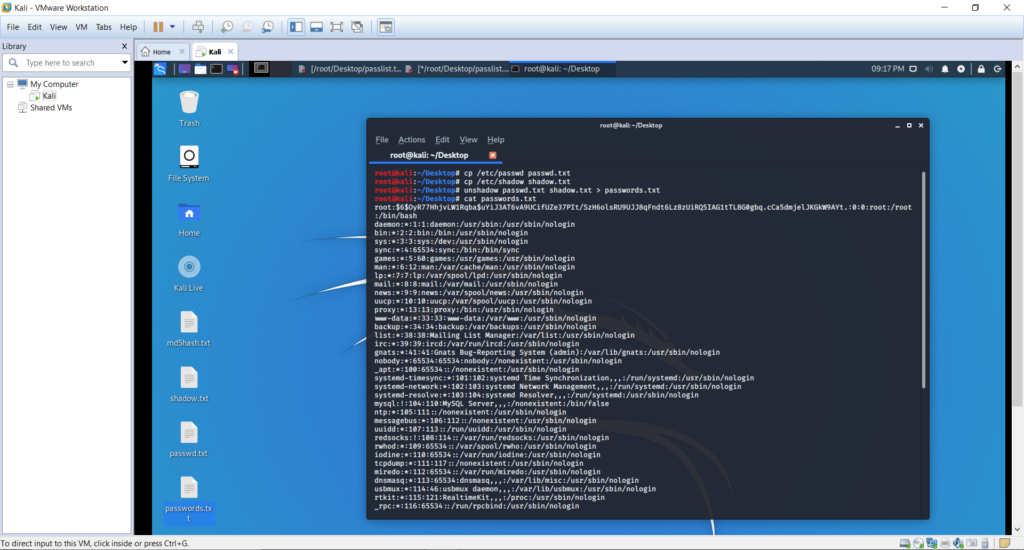
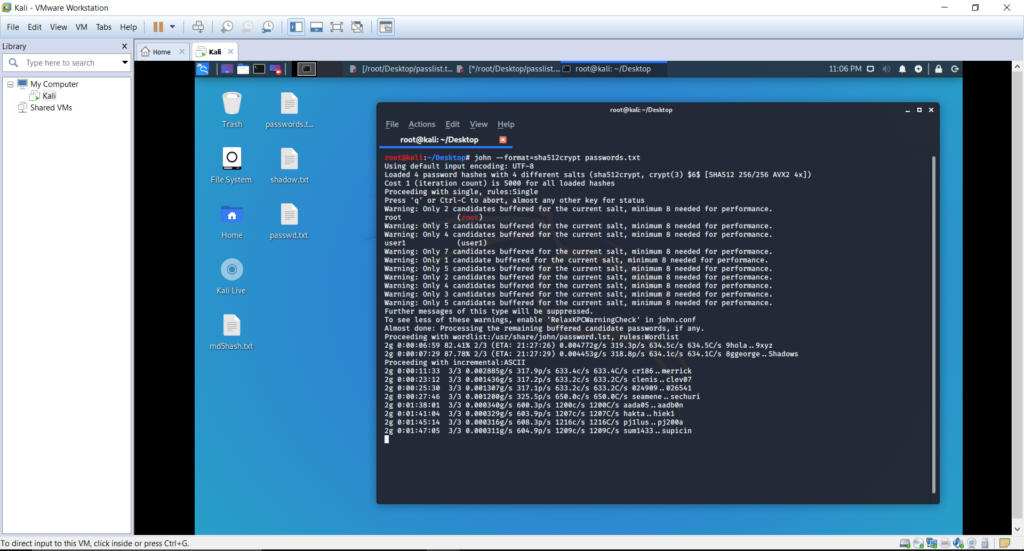
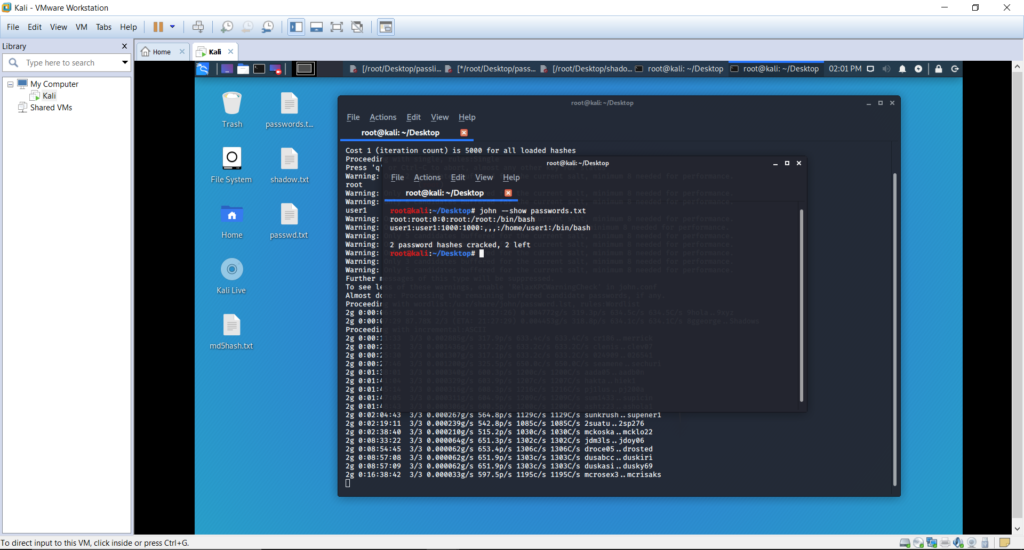
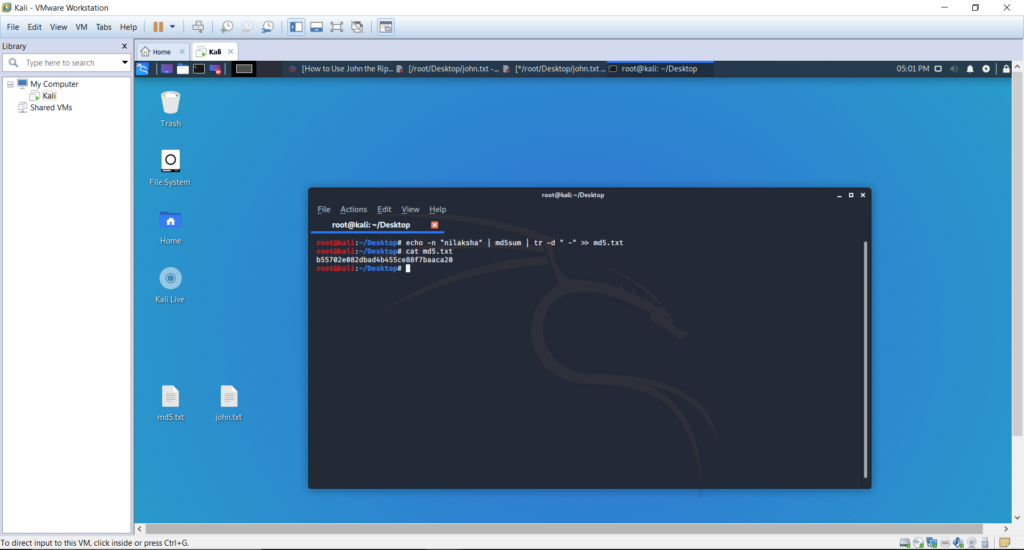
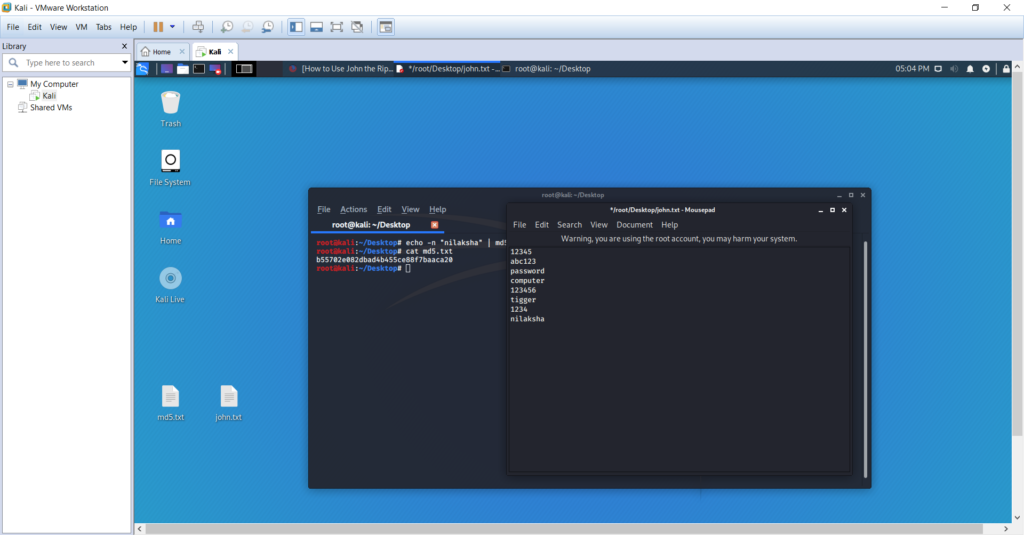
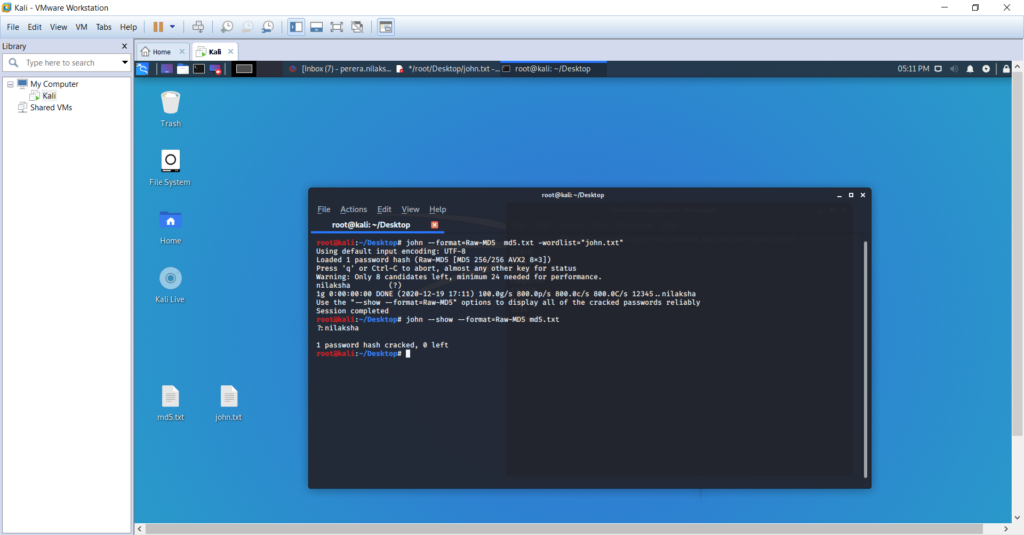
Sorry, but nothing matched your search terms. Please try again with some different keywords.
A tribute to the hatred!
At a point in life we all come across ones who has made it, making their way to making it, who stopped worrying about making it while they absolutely can, and all of them have a very interesting story to tell you.
Most of these guys have gone through the gift of long suffering or has gone through the stages in life the most uncommon ways. These are the ones who said “**uck it!” to the “stone carved system” and most probably messed up so bad but made a comeback in the most aggressive ways. During this time of their life they learnt the most weird things, picked up the most uncommon experiences in life and they saw things very different than the rest of the other.
In my eyes, most of these kinds of people are hated for a lot of reasons. But something struck me recently when I started to think about “how the hell can I make it!”?. “They all did the right thing!” no matter how tough of a decision it was, how much of a manipulation it was, they took these decisions and that worked for them. Then they realized, it had to be that way to secure their primary targets. The hate I had for them didn’t leave but it added up some sort of respect to this pile of hate. Because it was wrong in my mind and it was absolutely correct in their minds.
My first favorite most hated person I knew (I really don’t) was someone called “The mentor” a clever guy from a second generation hacker group. I got to know his a few hours later I got my hands to the global network! when I was a little kid. I didn’t know his real name neither where he lived. I don’t even know he loved himself more than his passion of doing the right thing. I don’t know if he is in prison or homeless or sipping tequila in a sunny beach somewhere in the Fiji islands! He got arrested doing the “right thing!” and what he had to say struck me harder than a brick and I seek no forgiveness for what I feel right feels wrong for you. In the end of the day, we’re all alike…
=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
The following was written shortly after my arrest…
\/\The Conscience of a Hacker/\/
by
+++The Mentor+++
Written on January 8, 1986
=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=-=
Another one got caught today, it’s all over the papers. “Teenager
Arrested in Computer Crime Scandal”, “Hacker Arrested after Bank Tampering”…
Damn kids. They’re all alike.
But did you, in your three-piece psychology and 1950’s technobrain,
ever take a look behind the eyes of the hacker? Did you ever wonder what made him tick, what forces shaped him, what may have molded him?
I am a hacker, enter my world… Mine is a world that begins with school… I’m smarter than most of the other kids, this crap they teach us bores me…
Damn underachiever. They’re all alike. I’m in junior high or high school. I’ve listened to teachers explain for the fifteenth time how to reduce a fraction. I understand it. “No, Ms. Smith, I didn’t show my work. I did it in my head…”
Damn kid. Probably copied it. They’re all alike.
I made a discovery today. I found a computer. Wait a second, this is cool. It does what I want it to. If it makes a mistake, it’s because I screwed it up. Not because it doesn’t like me…
Or feels threatened by me…
Or thinks I’m a smart ass…
Or doesn’t like teaching and shouldn’t be here…
Damn kid. All he does is play games. They’re all alike. And then it happened… a door opened to a world… rushing through the phone line like heroin through an addict’s veins, an electronic pulse is
sent out, a refuge from the day-to-day incompetencies is sought… a board is found.
“This is it… this is where I belong…” I know everyone here… even if I’ve never met them, never talked to them, may never hear from them again… I know you all… Damn kid. Tying up the phone line again. They’re all alike…
You bet your ass we’re all alike… we’ve been spoon-fed baby food at school when we hungered for steak… the bits of meat that you did let slip through were pre-chewed and tasteless. We’ve been dominated by sadists, or ignored by the apathetic. The few that had something to teach found us will-ing pupils, but those few are like drops of water in the desert.
This is our world now… the world of the electron and the switch, the beauty of the baud. We make use of a service already existing without paying for what could be dirt-cheap if it wasn’t run by profiteering gluttons, and you call us criminals. We explore… and you call us criminals. We seek after knowledge… and you call us criminals. We exist without skin color, without nationality, without religious bias… and you call us criminals. You build atomic bombs, you wage wars, you murder, cheat, and lie to us
and try to make us believe it’s for our own good, yet we’re the criminals.
Yes, I am a criminal. My crime is that of curiosity. My crime is
that of judging people by what they say and think, not what they look like. My crime is that of outsmarting you, something that you will never forgive me for.
I am a hacker, and this is my manifesto. You may stop this individual, but you can’t stop us all… after all, we’re all alike.
+++The Mentor+++
Tribute to the hatred! We’re all alike.